DJI has been at the center of ongoing questions about data security, privacy, and how its drones handle user information. For years, researchers and pilots have debated whether DJI collected more data than it admitted. That debate grew louder when DJI removed its flight-log sync feature, code-named Supervisor. Many saw this as an indirect confirmation that the system worked exactly as earlier reports described.
In an effort to stop the proposed DJI Ban, DJI announced the removal of its flight log sync feature on DJI’s own blog. Yet few drone pilots truly understand why this is a monumental admission by DJI. For years, there has been evidence of the “DJI Hack,” first forensically identified by Kevin Finesterre back in 2017.
In November 2025, an independent review added new clarity. The DJI Security Assessment, published by sUAS News, examined DJI’s software, data practices, and security controls. The assessment confirmed that DJI’s system can send a wide range of telemetry and user data unless pilots operate in strict offline modes. It also aligned with several concerns that researchers first raised years ago about DJI’s data pipeline and internal access.
This article will highlight how DJI collected data from its drones and what the Supervisor system did with it. We’ll also explore how the new 2025 security assessment supports many of the earlier concerns. By the end, you will understand what the “DJI hack” involved and why it still matters today.
Why Removing Flight-Log Sync Matters
On June 7, DJI removed the flight sync app from all its drones, a move that shocked many pilots. Known internally as Supervisor, this feature sent flight activity and device information straight back to DJI. For years, some pilots insisted there was no evidence of data collection issues, but turning off this feature proved otherwise.
The timing was significant. DJI was facing a potential ban to be voted on June 12th.
The company had urged pilots to speak up through the Drone Alliance. But U.S. lawmakers then questioned the Alliance itself, putting pilots in the middle of the debate.
Many pilots had already called out DJI, urging the company to acknowledge its security concerns.
Amid this serious scrutiny by Congress, removing flight-log sync signaled that the feature played a bigger role than most realized.
Flight-log sync was a key path for data collection. Information gathered via the Supervisor could feed into Sentinel, another internal system that tracked sentiment and influenced DJI’s market strategy.
According to the 2025 sUAS News DJI Security Assessment, this feature was part of a broader data pipeline. While it doesn’t accuse DJI of wrongdoing, it shows the feature carried real risks, and DJI knew about it. For pilots, the move was a tacit admission that concerns raised since 2017 had merit, marking a turning point in the ongoing debate over drone security.
How the Supervisor and Sentinel Worked
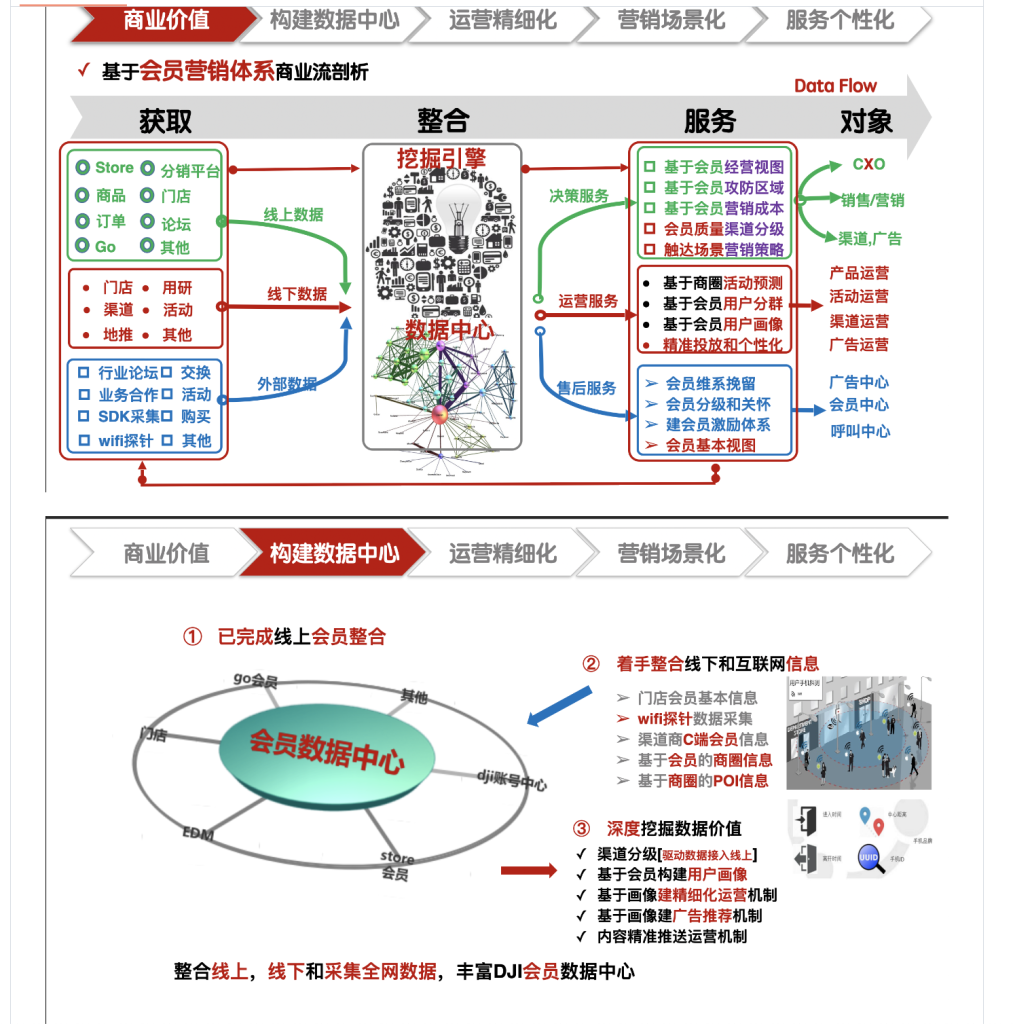
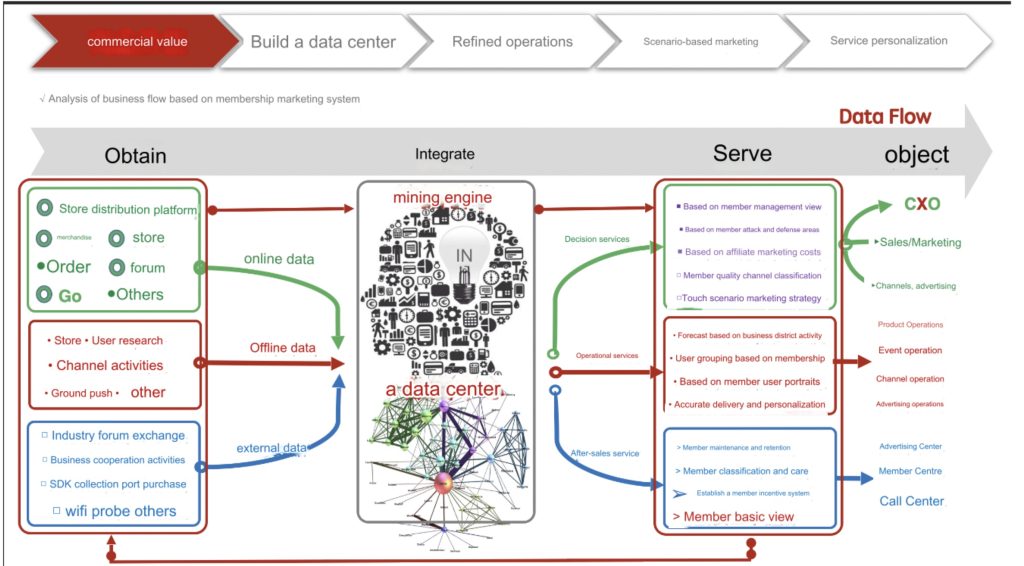
DJI relied on two internal systems—Supervisor and Sentinel—to manage and analyze data. Each had a distinct role, but together they created a comprehensive view of how pilots used DJI products.
Supervisor collected flight activity, device details, locations, and app data. It pulled this information from DJI apps and sent it to DJI servers, tracking how often drones flew, where they operated, and what devices were used. Each drone was assigned a unique ID, making it easy to connect activity to a specific aircraft.
Sentinel, on the other hand, focused on public sentiment and online activity. It monitored forums, social media, and other channels to gauge opinions about DJI. This allowed the company to respond to criticism, spot trends, and understand broader user behavior.
Together, Supervisor and Sentinel gave DJI detailed insights into its users. They weren’t simple support tools; they were part of a larger data pipeline linking aircraft activity with online behavior and cloud services.
The problem was that DJI used the sentiment analysis tool and fake profiles across social media to manipulate the brand into the cornerstone of drone products. DJI also used its data-gathering tools to steal patents and infringe on American drone manufacturers.
If you think about it, it’s very simple. DJI drones were the go-to tool for videography. Even DJI drones were used to film other drones completing missions, testing, and researching. One American company caught DJI in the Act, sued, and won.
Proof of DJI Supervisor Program.
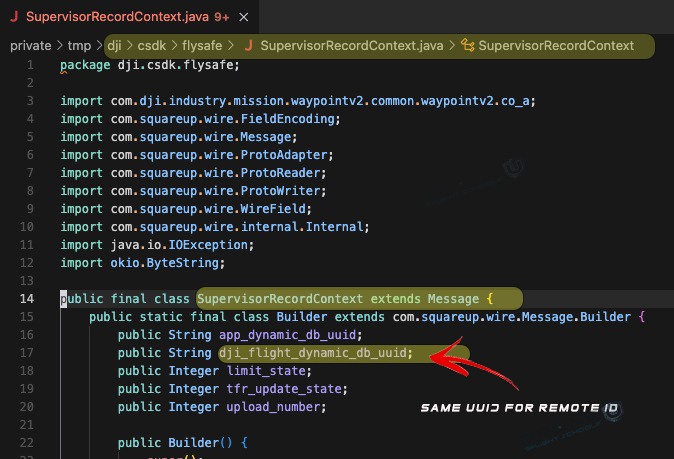
Believe it or not, if you plug in your DJI drone into a tool you can download online, you can see that the Supervisor program is built into your drone.
When you connect a DJI aircraft to certain analysis tools, the firmware shows references to Supervisor running in the background. These tools also reveal that Supervisor uses DJI’s SDK to send telemetry and device IDs to DJI’s servers.
Earlier versions of this system used cloud features like the “DJI Academy” log-sync channel and later FlightHub. Developers have shown that FlightHub’s source code can still be downloaded and rebuilt. This makes it a clear example of how DJI designed its cloud workflow.
You can even see in the photo above what parameters were even sent to DJI through the code.
One detail that raised concern is the DJI UUID. This is the same identifier used in the FAA’s Remote ID broadcasts. Seeing it inside the supervisor’s data flow led pilots to question how these identifiers were being used.
The 2025 sUAS News DJI Security Assessment supports this understanding. It confirms that DJI’s architecture has several points where telemetry and device IDs can leave the aircraft. The report also explains that “zero-egress” operation is possible, but only when pilots set strict, non-default configurations.
Who had access to the DJI Data?
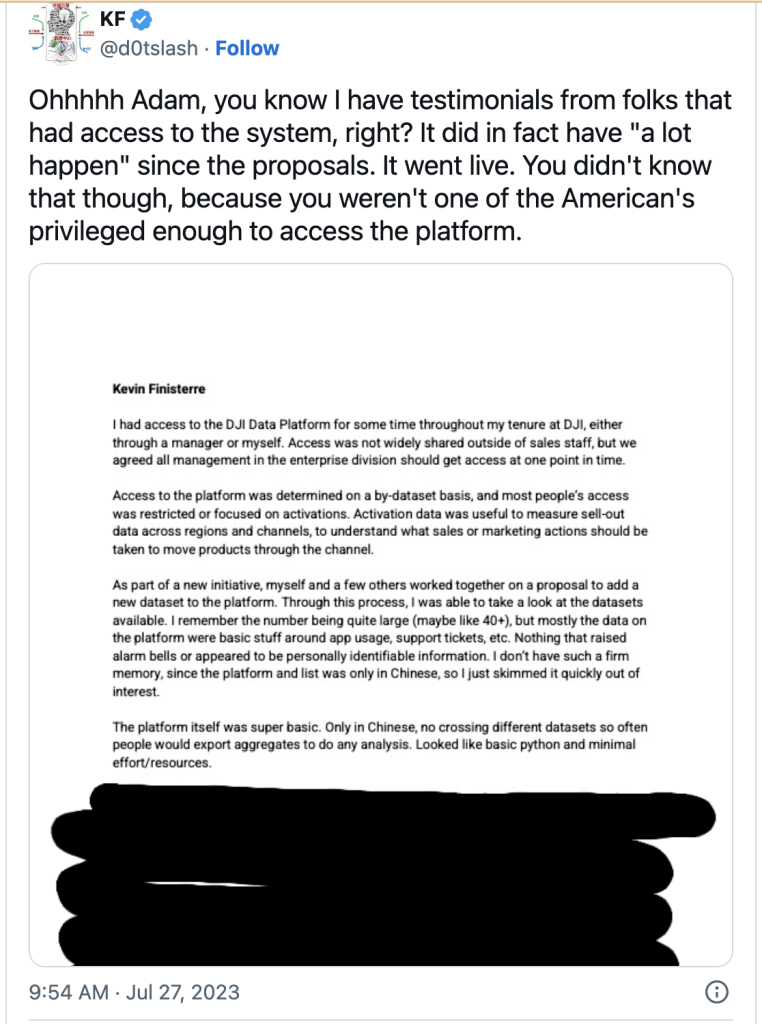
Thanks to a testimonial from a DJI employee, we know that about 146 different terminals and 72 different people at DJI had access to all this data being collected on drone pilots. It was used for sentiment analysis, marketing, sales, and even driving conversations online through prominent Facebook groups.
Here is a testimonial posted to Twitter from years ago explaining that not only did they have access to the data, but also what they did with the data.
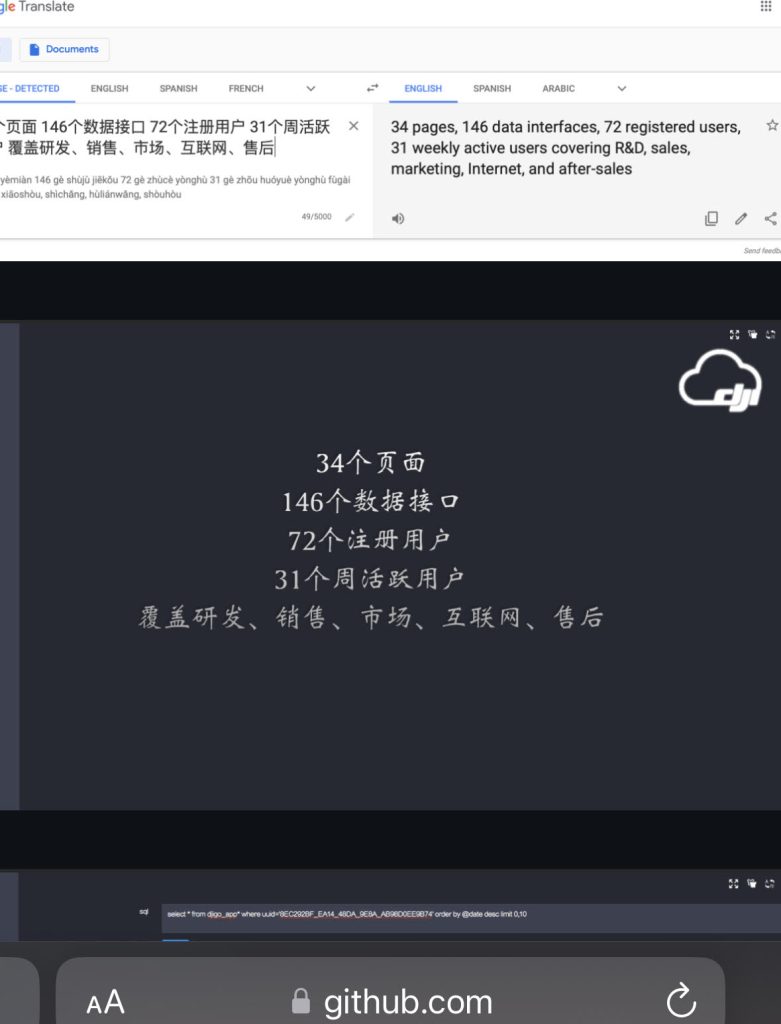
According to an internal Slide show highlighting how the DJI supervisor and Sentinel data platforms worked, DJI had 31 employees watching the data every WEEK. 72 total employees had access to the data, and there were 146 different data interfaces to interpret and review data.
This presentation matched the structure described in the 2025 assessment, which noted that DJI assigns different access roles across several internal teams.
The assessment does not say these teams misused pilot data. Instead, it highlights that DJI’s access controls are unclear and that the company has not shown how it limits or audits internal visibility.
This keeps the original concern in place: once the data enters DJI’s system, it is difficult to know exactly who can see it or how broadly it is shared inside the company.
What’s Included In the DJI Data Hack?
The supervisor program was created to gather as much intelligence on drone pilots, as it was designed to gather information on what they were flying. From that same DJI slide show, which was created in 2017, we can see exactly how DJI was gathering information from DJI apps, products, and even during conferences. (Notice the lower right-hand corner of how UUIDs were used to identify people at conferences.)
Now let’s show it in English.
What Does DJI Want With My Data?
When addressing the question “What does DJI want with my data?”, it’s important to clarify that DJI isn’t specifically interested in the personal details of individual pilots. Instead, the focus is on the data generated from the actions and usage patterns of drone pilots.
In this data leak, there are THOUSANDS of examples of driver’s licenses, passports, identification cards, and more personal data treasure trove for DJI to use however they want to.
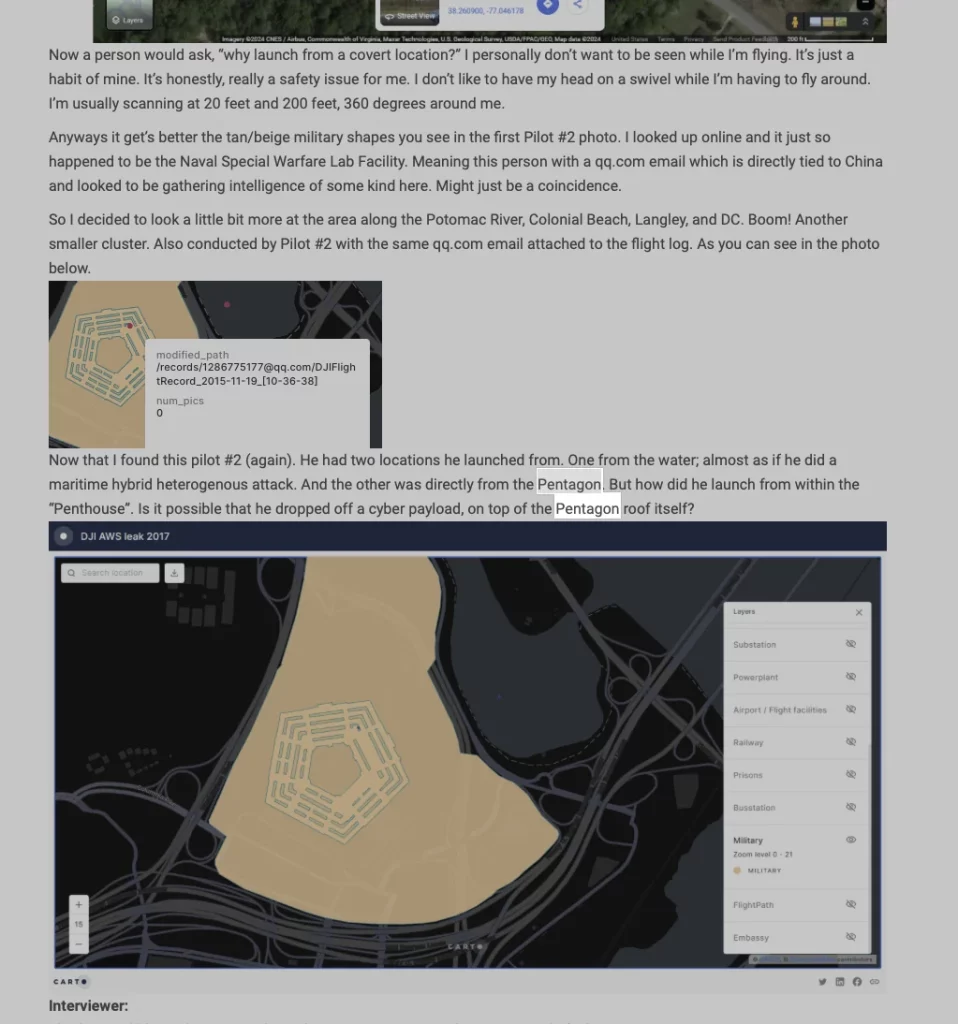
What might be even scarier is how DJI drones were collecting data on military installations when pilots flew them in areas they weren’t supposed to fly them.
There are countless examples of data gathered by DJI. They gathered thumbnail images from every single photo ever taken. They logged GPS data of where drone pilots took off from and helped create a vivid picture of secure locations.
Even when the US government was researching with DJI drones, all of that data went to DJI and thus the CCP. Imagine federal agents are trying to figure out exactly how “bad people” could gain access to critical information or cause serious destruction to some of our most important buildings and infrastructure. Well, one piece of data showcases how pilots figured out how to take off and fly over the Pentagon. All of this data was pulled from the open AWS server on which DJI was storing this data. Hacker Kevin Finnesterre figured out exactly how the data was mined and where it was stored.
How Would This Admission Impact the DJI Ban?
DJI’s decision to remove flight-log sync changed the debate around a possible U.S. ban. It showed the company knew this feature carried risk. It also confirmed that the data pipeline was real, which strengthened concerns raised by lawmakers and pilots. This timing made regulators pay closer attention and pushed the ban conversation forward.
Here’s a detailed breakdown of the situation:
1. Renewed Pressure on Congress
Lawmakers already questioned DJI’s data practices. The removal of sync during an active investigation made them take a harder look. It also raised new questions about how much data DJI collected and how the company used it to shape the market.
2. Confirmation That Past Concerns Weren’t Exaggerated
For years, DJI dismissed warnings about Supervisor, cloud telemetry, and internal data access. The change in June made those warnings harder to ignore. Regulators now see these issues as structural, not rumors or misunderstandings.
3. DJI’s Influence on U.S. Drone Policy
DJI used its position in the market to shape FAA rules around connectivity and Remote ID. These rules made constant data transmission normal for many drones. This influence now looks more significant because the systems that fed DJI’s internal tools depended on those data flows.
4. Broader Government Action on Drones
In June 2025, the U.S. signed new executive orders to boost domestic drone manufacturing. These orders tell federal agencies to use American-made drones whenever possible. They also push the industry to build safer systems, reduce foreign dependence, and strengthen airspace security. The government made it clear that it wants U.S. companies to grow fast enough to compete with DJI. This shift adds pressure to the ban debate because it shows Washington is preparing for a future with fewer Chinese-built drones in federal use.
5. Support for U.S. Drone Manufacturers
A ban would create a large gap in the market. Lawmakers may respond by supporting American drone companies with grants, loans, and tax incentives. The government could also invest in research so domestic manufacturers can close the technology gap. Regulators may ease barriers for new manufacturers so they can grow faster. These steps would help the U.S. build its own drone ecosystem instead of relying on DJI.
The admission of the flight sync issue raises questions about the extent of their influence and the ethical implications of their strategies.
How will other drone manufacturers respond to this situation? Will they be able to leverage the controversy to gain market share?
Will the FAA and other regulatory bodies revise their policies in light of these revelations? How will this affect future drone regulations and market dynamics?
The admission would not end DJI’s influence overnight, but it would change the political landscape. DJI’s change may help regulators see the risks more clearly. It also sets the stage for stronger support of domestic manufacturers and a possible shift in U.S. drone policy.
What the 2025 Security Assessment Confirms
The 2025 sUAS News Security Assessment gives an independent review of DJI’s data-handling systems. It confirms that DJI’s security risks come from how the platform is built, not from one malfunction or one bug.
1. Data Can Leave Through Many Paths
The report shows that telemetry and device IDs can leave the aircraft through several channels. These channels include cloud updates, app features, and services that run in the background. These pathways exist by design, which means they stay active unless the pilot removes them.
2. Zero-Egress Requires Manual Setup
DJI drones can avoid sending data to the cloud, but only with strict settings that most pilots never use. Pilots must enable Local Data Mode, lock firmware, avoid cloud features, and manage networks. These controls require deliberate setup and do not come enabled out of the box.
3. Internal Access Controls Are Unclear
The assessment finds gaps in DJI’s internal data governance. It notes limited visibility into who inside DJI can view stored telemetry and device IDs. It also raises concerns about supply-chain transparency and how DJI servers handle user information.
4. Risks Come From System Design
The report does not accuse DJI of wrongdoing. Instead, it explains that the platform’s architecture naturally exposes data when pilots use normal settings. This matches years of concerns about how DJI handles telemetry and identifiers.
5. The Findings Match Earlier Disclosures
The assessment aligns with previous reports from 2017 onward. It confirms that the same risks remain in newer products because the core design has not changed.
What This Means Going Forward
The 2025 security assessment confirms that DJI’s core data risks still exist. DJI can reduce exposure, but only when pilots apply strict settings that most users never enable. This gives regulators and operators a clearer view of DJI’s true security posture.
Zero-egress operation is possible, but rare. Most pilots leave cloud sync and app features on, which allows data to flow during normal flights.
For military, government, and critical-infrastructure use, the risk remains high. No current configuration fully isolates telemetry or device identifiers. These findings also strengthen calls for tighter oversight and increased investment in domestic drone alternatives.
Because security now depends on how drones are configured and operated, pilots and organizations need to understand more than just how to fly.
Are you confident your drone operations are secure and compliant? Not sure?
Become a DroneU member to learn how to manage drone data, reduce risk, and stay compliant.
Frequently Asked Questions
1. How Does the 2025 Security Assessment Change Our Understanding of DJI Risks?
The 2025 Security Assessment confirms that DJI’s security issues are structural, not accidental. Telemetry, cloud reliance, and internal access create ongoing risks even when pilots follow some mitigation steps.
2. Can Pilots Stop DJI Drones From Sending Data?
Yes, but only with strict settings.
Local Data Mode, locked firmware, and avoiding cloud features can prevent data from leaving the drone. Most users do not enable these settings, so zero-egress is uncommon.
3. Can U.S. Drone Manufacturers Realistically Replace DJI if a Ban Happens?
Government support, including grants, R&D, and regulatory incentives, is designed to help domestic companies scale. It will take time for U.S. manufacturers to match DJI’s technology and market reach.
4. How Does DJI’s Admission and the 2025 Assessment Affect the Potential U.S. ban?
The admission and 2025 assessment give regulators and lawmakers fresh evidence. They confirm structural risks and support stricter oversight, possible bans, and preference for U.S.-made drones.





Add Your Comment